Table of Contents
Let's Encrypt + Proftpd
Документация ProFTPD: http://www.proftpd.org/docs/howto/TLS.html / http://www.proftpd.org/docs/contrib/mod_tls.html
Мой рабочий конфиг для CentOS 7, ProFTPD 1.3.5 и OpenSSL 1.0.2k
TLSEngine on TLSRequired on TLSProtocol TLSv1.2 TLSCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384 TLSRenegotiate none TLSVerifyClient off TLSLog /var/log/proftpd/tls.log TLSRSACertificateFile /etc/letsencrypt/live/rtfm.wiki/cert.pem TLSRSACertificateKeyFile /etc/letsencrypt/live/rtfm.wiki/privkey.pem TLSCertificateChainFile /etc/letsencrypt/live/rtfm.wiki/chain.pem TLSDHParamFile /etc/ssl/certs/dhparam4096.pem
Cipher list взял с сайта Mozilla
Если нет файла DH
openssl dhparam -out /etc/ssl/certs/dhparam4096.pem 4096
Удобнее добавить эти настройки для TLS в отдельном файле через Include в /etc/proftpd.conf
Include /etc/proftpd_tls.conf
Проверка
/var/log/proftpd/tls.log
2020-01-12 01:43:11,588 mod_tls/2.6[22465]: TLS/TLS-C negotiation failed on control channel 2020-01-12 02:25:10,230 mod_tls/2.6[24365]: TLS/TLS-C requested, starting TLS handshake 2020-01-12 02:25:10,557 mod_tls/2.6[24365]: client supports secure renegotiations 2020-01-12 02:25:10,558 mod_tls/2.6[24365]: TLSv1.2 connection accepted, using cipher ECDHE-RSA-AES256-GCM-SHA384 (256 bits)
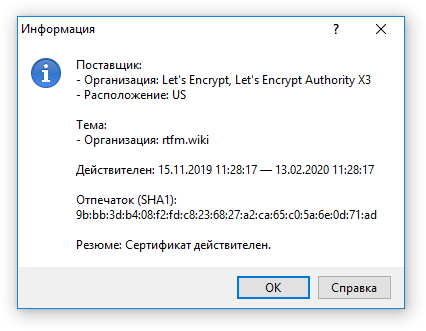
Информация о подключении в WinSCP
Проблема в Filezilla

Что это значит (всё ок!)
Also, keep in mind that Filezilla doesn’t check the CAs that your OS trust so you need to manually trust it in the first connection. No matter whether it is a self-signed certificate, a Let’s Encrypt cert or a commercial one, in all of them, in the first connection, you need to trust the certificate.
The only thing you can do is trust the certificate. It is a Filezilla “feature” it doesn’t check the CAs that your OS trust so you need to manually trust it in the first connection. No matter whether it is a self-signed certificate, a let’s encrypt cert or a commercial one, in all of them, in the first connection, you need to trust it.
Self-signed
Самоподписанный сертификат. Описание ключей в документации openssl.
openssl req -x509 -nodes -sha256 -days 365 -newkey rsa:4096 -keyout /etc/ssl/certs/proftpd.key -out /etc/ssl/certs/proftpd.crt
Прочее
На будущее осталось разобраться в опциях TLSCACertificateFile и TLSCertificateChainFile. Единственный топик в сети порождает еще больше вопросов.


Discussion